We've always been committed to improving security and performance across SFTP To Go. Along with pushing our limits, we're taking a vital step to keep your account safer than ever!
What’s Changing?
Starting December 7, 2025, we will be requiring Multi-Factor Authentication (MFA) for all Admin users on SFTP To Go. This is focused on securing management actions. MFA will not be required for credentials used to access file storage (although we highly recommend adding it for human users).
This change is part of our ongoing commitment to a more secure platform, and we’re excited to make this enhancement for your protection.
How Does This Affect You?
- If you are NOT an Admin user: This change does not affect you. You can continue to use your SFTP To Go account as usual.
- If you are an Admin user AND already have MFA enabled: Great job! This change will not affect your workflow.
- If you are an Admin user AND do not have MFA enabled: Starting December 5, you will be required to enable MFA when you sign in your SFTP To Go admin dashboard using user/password or social connections (e.g. Google, Github). We recommend setting up MFA even before December 5, using an authenticator app.
What’s new?
SFTP To Go now supports SAML based authentication for your organization, with popular identity providers such as Okta, Entra ID, Google Workspace, custom SAML or OIDC and more. This is enabled for our enterprise customers. Contact us by replying to this email to get more information.
What is SAML SSO?
Many companies already leverage SAML SSO. It's how you use your company's central login (Microsoft, Google, Okta, etc.) to access third-party services.
SAML (Security Assertion Markup Language) is the open standard for swapping authentication and authorization data. SSO (Single Sign-On) lets users sign in just once and then access multiple systems without constantly re-entering their credentials.
How to enable SAML SSO?
Setting up SAML is straightforward. Any enterprise plan organization administrator can enable this feature by following these steps:
- Go to your organization’s settings tab.
- Scroll down to the Team section and expand Single Sign-On (SSO).
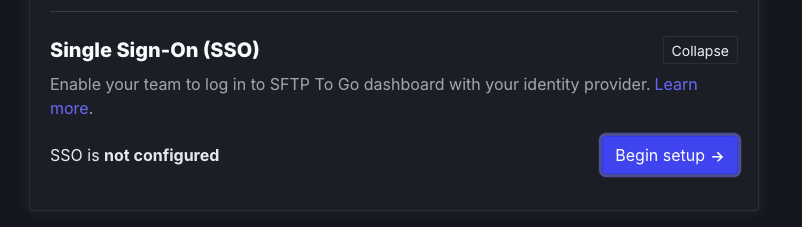
- Click Begin Setup.
- Follow on-screen instructions to set up your IdP (Identity provider).
- Once you finish setting up your IdP, use the toggle to enable or disable JIT (Just-in-time) provisioning. This defines whether you have to first invite a team member from within your SFTP To Go organization, or if only your identity provider defines who can access the organization.
- Copy the SSO login link (unique per organization) and share with your team for SSO authentication.