A note to our users: SFTP To Go is not affected by the WS_FTP vulnerabilities because we don't use the WS_FTP product. We prioritize tried and tested protocols combined with robust and layered security measures. Our regular testing and update schedule ensures zero entry points or vulnerabilities.
It was cause for pause in September 2023, when Progress Software announced that their WS_FTP Server, a household name in file transfer, had turned up riddled with vulnerabilities.
If the name “Progress Software '' sounds familiar, that’s because it’s the same company who developed MOVEit file transfer platform, which was subject to the LEMURLOOT or CL0P SQL attack in July this year.
That was a devastating zero-day vulnerability exploitation that touched 2095 companies and breached the data of more than 62 million people.
In spite of the gravity of the previous case, the latest WS_FTP vulnerabilities weren't exactly minor hiccups; they were significant holes that could potentially let attackers wreak havoc on any systems overdue for an upgrade.
The most critical WS_FTP vulnerabilities (out of 8 vulnerabilities found)
Critical status:
- CVE-2023-40044: This isn't just another vulnerability on the list. It's a .NET deserialization issue in the WS_FTP Server Ad Hoc Transfer module, allowing pre-authenticated attackers a golden ticket to execute commands directly on
- CVE-2023-42657: Directory traversal might sound benign, but in the hands of a skilled malicious party, it's a potent weapon. This vulnerability lets attackers meander outside their authorized WS_FTP folder path, potentially escaping the WS_FTP Server file structure altogether.
Other vulnerabilities worth noting:
- CVE-2023-40045 to CVE-2023-40049: These range from the somewhat irritating reflected XSS in the Ad Hoc Transfer module to the more insidious file enumeration vulnerabilities in the WebServiceHost directory listing.
The unfolding events
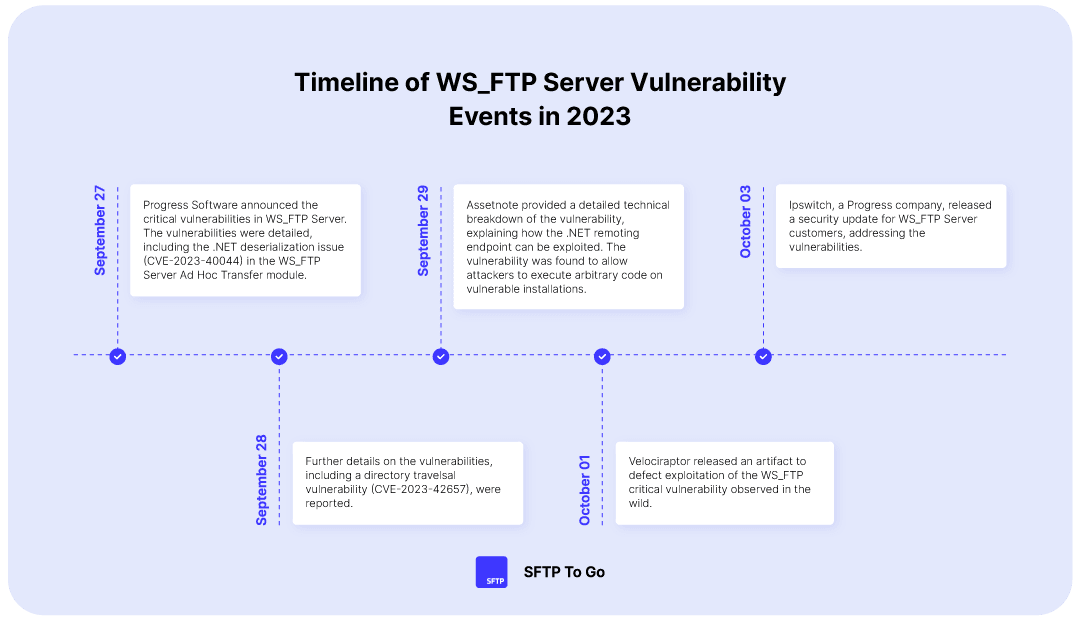
So, on 27 September 2023, Progress said this to its (give or take) 40 million users, outlining a total of 8 vulnerabilities, 3 medium, 3 high, and 2 critically severe in the supposedly secure WS_FTP.
Days after the patches were released, Progress declared that there had been “no evidence of exploitation at this time”, but it seems they spoke too soon.
By the end of September (that is, 3 days later), the research team at Rapid7 became the first to detect what they termed “mass exploitation attempts” on WS_FTP’s many perforations, spanning various countries, and even more WS_FTP instances.
Now, while updates were undertaken and the volume of exploit attempts is currently low, telemetry data from AssetNote indicates that around 2,900 hosts run the WS_FTP software.
These hosts span large enterprises, governments, and educational institutions, and many of these servers represent entire networks that are now, essentially, exposed.
Exploitation Patterns
The attack pattern, as observed by Rapid7, began on the evening of September 30 with multiple alerts from different customer environments that were triggered almost simultaneously, suggesting a coordinated attack.
The exploit chain was consistent across incidents, hinting at a possible orchestrated mass-scale exploitation of WS_FTP vulnerabilities.
Takeaways included:
- A single Burp Suite domain was consistently used in every exploit attempt, suggesting a single actor behind these attacks.
- The exploit chain involved the execution of NTUSER.dll, believed to be associated with Bishop Fox's red-team post-exploitation kit, Silver.
Understanding the risks
The fact is that, while there are a veritable spoil of file transfer options (like WS_FTP) available, the “spice of life” that variety brings can turn out to be quite unsavory.
The potential hidden risks around the numerous transfer solutions on the market include:
- Lack of transparency: Many file transfer solution providers operate as closed-source systems. This lack of transparency can make it challenging to ascertain the security measures in place, leaving users like you in the dark about potential vulnerabilities.
- Inconsistent updates: Regular updates are the foundation of software security. Some providers might not prioritize timely patches, leaving systems exposed to known vulnerabilities for extended periods.
- Complexity and customization: While customizable solutions sound appealing, they can also mean inadvertent security gaps. The more complex a system, the harder it becomes to ensure every nook and cranny is secure.
- Legacy systems: Some solutions in the market have been around for ages and might still be relying on outdated protocols or encryption standards, making them more susceptible to modern-day threats.
- Limited scalability: As businesses grow, so do their data transfer needs. Solutions that don't scale efficiently can lead to workarounds or makeshift solutions, which can inadvertently introduce security risks.
The broader picture
For those shoulder-deep in tech and communications, these vulnerabilities drive home the perennial challenges of software security and maintenance.
It's not just about patching up the present vulnerabilities, it’s about anticipating potential future threats as well, including system shutdowns, data breaches, and malware propagation.
An attacker with access to a server's OS is like a very quiet bull in a china shop, the implications are costly and concerning. In the wake of WS_FTP's vulnerabilities, it's certainly worth spotlighting solutions that prioritize security without compromising on functionality—like SFTP To Go.
SFTP To Go's security blueprint:
- Diverse secure protocols: Beyond just SFTP, SFTP To Go harnesses a gamut of standard protocols, including FTPS, Amazon S3, and HTTPS. It's about ensuring a fortress-like environment for file access and transfers.
- Leveraging AWS: With its foundation on Amazon Web Services (AWS), SFTP To Go brings a multi-AZ architecture, ensuring that data isn't just secure but also readily available, and that operations are easily, instantly scalable.
- Regular testing: SFTP To Go prioritizes continuous improvement, including regular updates and testing. Testing is conducted both by our in-house security team and by third-party experts.
In conclusion
The WS_FTP vulnerabilities and subsequent attacks are a cautionary tale of the challenges in data transfer security. Yet, they also highlight the importance of staying updated and choosing the least complex but most secure solutions.
For the tech community, it's not just about innovation and making our digital fortresses impregnable, but about securing our assets (and data!) while they’re in transit.
Our straightforward multi-AZ architecture enhances availability without compromising on security. Our regular testing and update schedule ensures zero entry points or vulnerabilities.

Frequently Asked Questions
Is SFTP To Go affected by the WS_FTP vulnerabilities?
No, SFTP To Go is not affected by the WS_FTP vulnerabilities because it does not make use of the WS_FTP product. Instead, SFTP To Go opts for tried and tested protocols and security measures in a simple multi-AZ architecture that ensures zero entry points or vulnerabilities. These measures and protocols include SFTP, FTPS, Amazon S3, and HTTPS, leveraging the robustness of Amazon Web Services (AWS), and providing APIs and webhook notifications for seamless integration.
What are the recent vulnerabilities discovered in WS_FTP Server?
WS_FTP Server has been found with multiple vulnerabilities, including:
CVE-2023-40044: A .NET deserialization issue in the Ad Hoc Transfer module.
CVE-2023-42657: A directory traversal vulnerability.
CVE-2023-40045: A reflected XSS in the Ad Hoc Transfer module.
CVE-2023-40046: A file enumeration vulnerability in the WebServiceHost directory listing.
[Other vulnerabilities not specified in detail.]
How serious is the CVE-2023-40044 vulnerability?
It's a significant vulnerability. It allows pre-authenticated attackers to execute commands directly on the server's operating system, posing a severe security threat.
What risks do these vulnerabilities pose?
Attackers can potentially gain unauthorized access, execute commands on the server's OS, move outside their authorized WS_FTP folder path, and exploit other vulnerabilities like reflected XSS and file enumeration.
What are the hidden risks of file transfer solutions like WS_FTP?
Risks include lack of transparency in closed-source systems, inconsistent software updates, complexity and customization leading to inadvertent security gaps, reliance on outdated protocols in legacy systems, and limited scalability leading to potential security risks.
What are the implications of an attacker gaining access to a server's OS?
An attacker with such access can cause significant damage. The implications are costly, including potential data breaches, system shutdowns, and malware propagation. Beyond that, there are significant privacy concerns, including access to personal data, intercepting of communications, compromise of user profiles, identity theft, and more. Of course, any of these could mean a loss of reputation for companies, and the risk of severe legal action.

