In the world of seamless data exchange, Electronic Data Interchange (EDI) takes the crown, connecting businesses across the globe. It's all in the numbers though, and research indicates clear and persistent market growth for the EDI software sector.
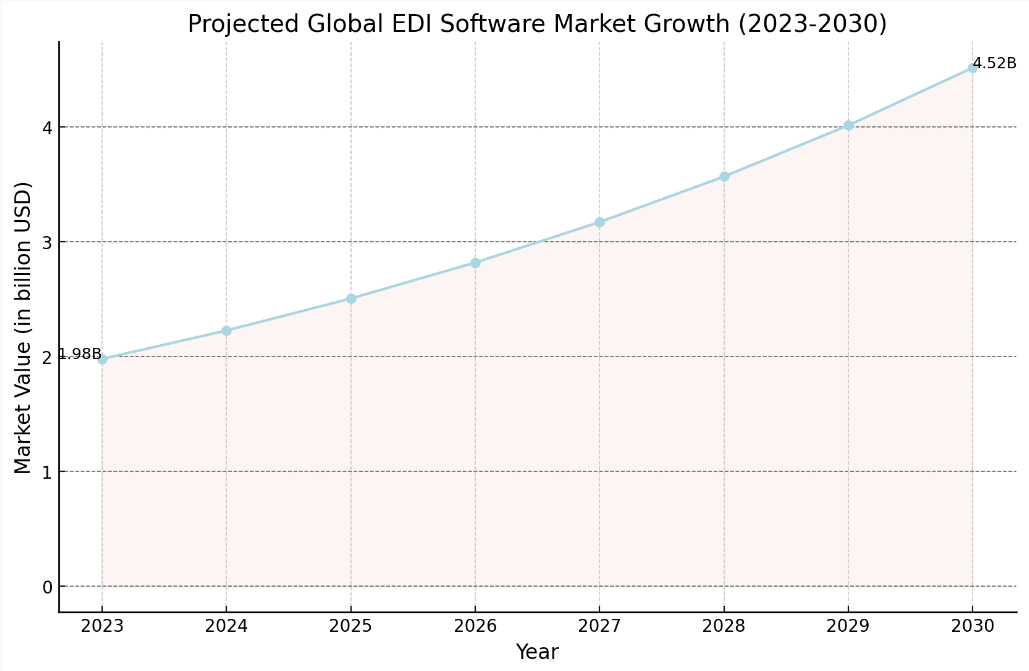
In fact, the market is expected to grow at a compound annual growth rate (CAGR) of 12,5%. Starting at 1.98 billion USD in 2023, it shows a steady increase, reaching a value of approximately 4.52 billion USD by 2030.
Now, when it comes to securely transferring your valuable EDI files, the Secure File Transfer Protocol (SFTP) is your best and most trusted option.
If you’ve been tasked with implementing EDI over SFTP, or if you’re trying to figure out whether EDI over SFTP makes sense for you and your organization, all sorts of questions arise. We’ve compiled this list of best practices to guide you through the maze of solving the intricate issues that may arise.
If you need a primer on EDI communication protocols, or if you’re still confused about the differences between SFTP and FTP or FTPS, you may want to read these before diving in.
For more on how EDI communication protocols can benefit your business, watch this quick intro from TrueCommerce.
EDI over SFTP: Pros, limitations, and solutions
When building an EDI over SFTP integration with a partner, you get the benefits of built-in security, simplicity, support for large file transfer, and drop-site neutrality, but you may miss some of the benefits of AS2 because SFTP is a generic file transfer protocol which was not intended solely for the use in B2B communication.
SFTP limitations and their workarounds:
Digital signatures allow you to check who authored the message (or file) and also make sure that it wasn’t tampered with.
Possible solution: They’re not part of SFTP, but you can use a protocol such as GPG to sign each file that you upload.
Receipt notifications (aka message disposition notifications or MDN in AS2) allow you to make sure that your business partner received and processed your EDI message.
Possible solution: As part of your data processing flow, for each file you download, upload a file with the same filename and an added suffix (e.g., .received). The file can either be empty or contain your GPG digital signature, if you'd like to be extra meticulous.
SFTP for EDI best practices
When looking at SFTP as the intermediate dropsite for EDI messages between partners, there are a few ways to make it more secure and more resilient:
1. Invest in redundant storage:
In many cases, files exchanged as part of EDI communication are relatively short lived (i.e. partner A uploads files, partner B downloads and processes said files, and besides keeping them for posterity, these files are no longer needed).
However, you should invest in redundant storage to make sure files don't go missing or end up corrupted within a transaction or that if you do intend to keep an archive on your SFTP server, these files remain intact.
2. Keep the SFTP server highly available:
This is easier said than done. As opposed to stateless servers such as HTTP servers, SFTP servers are meant to store files.
So, in order to make them highly available, you’d need to separate the servers from the storage (by using a network attached storage for instance, that can be accessible to multiple servers) and also from the public network interface (by using a network load balancer).
3. Implement user access management:
You can enhance the security of EDI and SFTP systems by ensuring that only authorized personnel can access and use sensitive data.
By assigning individual user accounts and defining access rights, you won’t have to deal with the headaches that come with unauthorized access and data breaches!
4. Chroot users:
Yep, you read that right. “change root” is a way to restrict users' access to parent folders in secure file transfer protocols like SFTP. When the user connects to the SFTP server, they will be assigned a specific home directory.
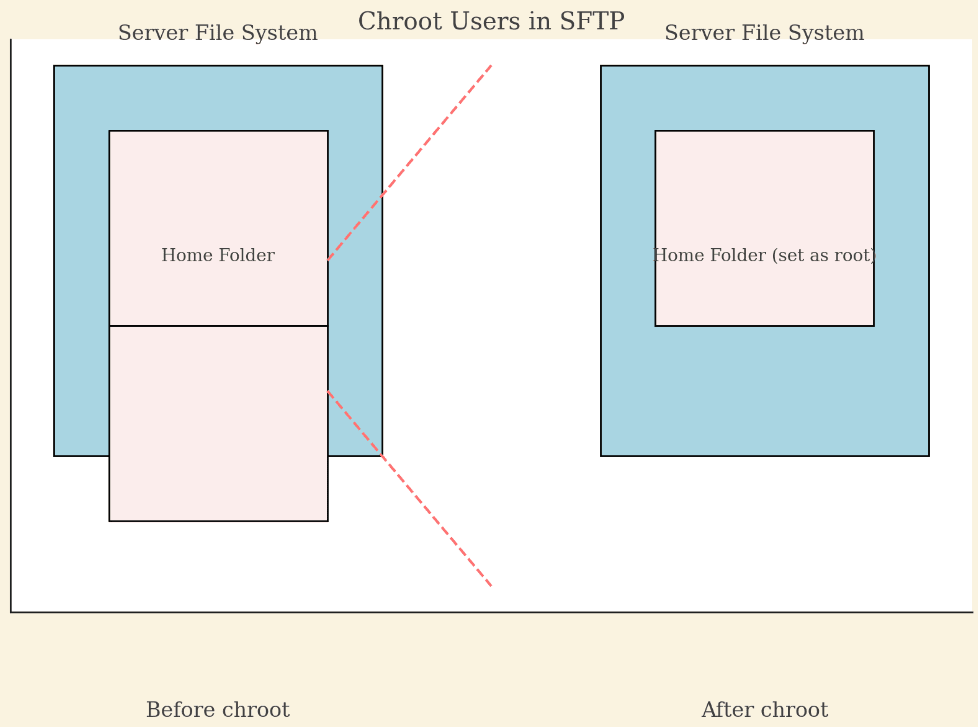
Chroot allows the server administrator to set a user’s home folder as their “root” folder, so they can’t even guess the folder structure besides what’s contained in their home folder, and it also prevents them from accessing the parent or sibling folders.
5. Rotate password regularly:
Enhance security and protect against unauthorized access by periodically changing user passwords at regular intervals.
While this may seem like a chore, password rotations help mitigate potential damage by limiting the window of opportunity for attackers to exploit compromised credentials.
6. Prefer public key authentication:
Passwords are old school. Increase security around authentication using SSH keys, a method that involves the use of a public key and a private key. The public key is shared with others, while the private key is kept securely by the user.
The key pair can then be used in what’s called asymmetric cryptography in which encryption is done with one key, and decryption with the other, and it’s not feasible to derive the encryption key from the decryption key (or vice versa).
7. Limit access to known IP addresses:
Prevent unauthorized access and reduce chances for malicious activity by limiting access to specific IP addresses.
Disable obsolete ciphers: Encryption algorithms (called ciphers), are algorithms that encrypt & decrypt data. To maintain the security of your data, it’s necessary to remove or disable ciphers that become obsolete over time (caused by vulnerabilities or flaws).
8. Encrypt data at rest:
SSH, and thus SFTP, make sure data is encrypted over the wire, but you should make sure that files are also encrypted at rest in storage, so that if the storage is physically compromised - the data won't be readable.
9. Monitor file access:
Use file access logs to check who uploaded, downloaded or deleted files and when.
10. Keep the SFTP server out of your private network:
Since at least two business partners intend to connect, upload, and download files from this server, this means that you may have to allow public access to the SFTP server, which will be frowned upon by your organization’s CISO.
There’s always the question of using a managed service (i.e. a cloud SFTP service) vs. building the solution yourself. We’ve done a comprehensive comparison here.

What is SFTP To Go and How Can We Help?
Keen to get all the best practices mentioned above out of the box and in a managed cloud service? Keen to focus on handling EDI messages, and adding digital signatures and receipt notifications? Check out SFTP To Go.
Some of the key benefits of our service (on top of the best practices mentioned above) include:
- User-friendly GUI that provides a centralized dashboard.
- Restful APIs to manage users, permissions, and other settings.
- Webhooks to get real-time notifications when files are uploaded (to allow much faster response time when partners upload files).
- Static IP addresses to allow easy access from restricted private networks.
- Personalized domain names to make the managed server your own
And a dedicated team to help you in every step of the way. Learn about automating SFTP to reduce human error and streamline workflows.
Frequently asked questions
What are EDI and SFTP?
EDI (Electronic Data Interchange) is a process that allows the exchange of business documents between different companies in a standardized electronic format.
SFTP (Secure File Transfer Protocol) is a secure method for transferring files over a network, leveraging SSH (Secure Shell) to ensure data security during transmission.
What are some EDI best practices?
Standardization: Adhere to industry standards such as EDIFACT or ANSI X12 for seamless communication.
Data Validation: Implement validation checks for data accuracy and completeness.
Error Handling: Develop robust error handling procedures.
Documentation: Maintain comprehensive EDI process documentation.
What are some SFTP best practices?
Encryption: Utilize strong encryption algorithms for data protection during transmission.
Authentication: Enhance security through multi-factor authentication.
File Integrity: Use checksums to verify file integrity during transfer.
Access Control: Establish strict policies to restrict unauthorized data access.
How can I ensure secure and efficient EDI transactions?
Backup: Regularly back up EDI data to prevent data loss.
Monitoring: Continuously monitor your EDI system for prompt issue detection and resolution.
Testing: Conduct regular tests with trading partners for smooth operations.
Compliance: Adhere to legal and industry regulations to maintain good relations with trading partners.
How can I enhance SFTP transfer security?
Updates and Patches: Regularly update the SFTP server and apply security patches.
Logging and Auditing: Maintain detailed logs of all SFTP transactions and conduct regular audits to ensure security and compliance.
Secure Connections: Use secure connections, such as VPNs, to enhance security during file transfers.
Endpoint Security: Ensure robust security measures at both the sending and receiving endpoints.
What tools are best for EDI and SFTP?
Various tools are available that facilitate the implementation of EDI and SFTP best practices. These include features like data encryption, secure file transfers, and automated monitoring and reporting. It is advisable to opt for well-established tools with good industry reviews.
How do I choose the right EDI and SFTP solutions?
Consider the following factors when choosing EDI and SFTP solutions:
- Scalability: The solution should grow with your business.
- Integration: Seamless integration with existing systems and workflows.
- Support and Training: Robust support and training from the provider.
- Cost: Consider the total cost of ownership, including setup, maintenance, and subscription fees.
Can EDI and SFTP processes be automated?
Yes, many EDI and SFTP solutions offer automation features that streamline processes, reduce manual errors, and save time. Features include scheduling file transfers, automating responses to common errors, and integrating EDI data directly into ERP or other business systems.
How do I maintain compliance with regulations in EDI and SFTP usage?
To maintain compliance:
- Documentation: Keep detailed records of all transactions.
- Training: Train your staff on compliance requirements and best practices.
- Regular Audits: Conduct regular audits to identify and address compliance issues.
- Legal Advice: Seek legal advice to understand the specific regulations applicable to your industry and region.